It’s an old draft from 2010. Recently I was designing a network which VSS was on the topics, so it reminded me of the draft.
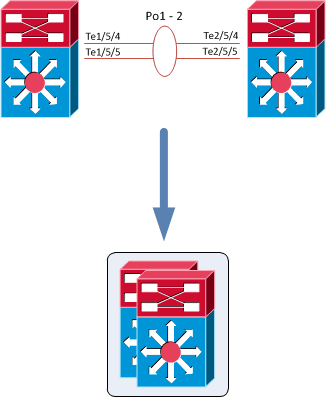
The Cisco Catalyst 6500 Series Virtual Switching System (VSS) allows the clustering of two chassis together into a single, logical entity. This technology allows for enhancements in all areas of network design, including high availability, scalability, management, and maintenance.
The Virtual Switching System is created by converting two standalone Catalyst 6500 systems to a Virtual Switching System. The conversion is a one-time process that requires a few simple configuration steps and a system reload. Once the individual chassis reload, they are converted into the Virtual Switching System.
All control plane functions are centrally managed by the active supervisor engine of the active virtual switch chassis, including:
- Management(Simple Network Management Protocol [SNMP], Telnet, Secure Shell [SSH] Protocol, etc.)
- Layer 2 Protocols (bridge protocol data units [BPDUs], protocol data units [PDUs], Link Aggregation Control
Protocol [LACP], etc.) - Layer 3Protocols (routing protocols, etc.)
- Software data path
The requirements to convert the 6500 into a Virtual Switching System are:
- The VSS requires Supervisor Engine 720 with 10-GigabitEthernet ports. You must use either two VS-S720-10G-3C or two VS-S720-10G-3CXL supervisor engine modules.
- The VSS requires 67xx seriesswitching modules.
- The VSLEtherChannel supports only 10-Gigabit Ethernet ports.